The rise of AI-powered cyberattacks is a growing concern for all individuals, businesses, and governments alike. It is rapidly transforming various aspects of our lives, from how we shop to how we work.
Imagine a world where cyberattacks are no longer limited by human capabilities. Where malicious software evolves at an alarming rate, effortlessly evading traditional defenses. Where phishing emails are so personalized and convincing, they become almost indistinguishable from genuine correspondence. This is not a dystopian future, but a rapidly approaching reality – the era of AI-powered cyberattacks.
Artificial intelligence, once a futuristic concept, is now being exploited by cybercriminals to launch increasingly sophisticated and devastating attacks. AI algorithms, with their ability to analyze vast amounts of data, identify patterns, and make predictions with remarkable accuracy, are being weaponized to automate and enhance cyberattacks in unprecedented ways.

This article delves into the alarming rise of AI-powered cyberattacks, exploring the various ways AI is being misused to amplify cyber threats. We’ll examine the consequences of these attacks, from data breaches and financial losses to operational disruptions and national security threats.
But this is not just a tale of doom and gloom. We’ll also explore the proactive measures that individuals, organizations, and governments can take to mitigate these risks and build a more secure digital future.
So, buckle up and prepare to explore the fascinating and concerning intersection of artificial intelligence and cybersecurity. This is a journey into the heart of a new battleground, where the future of our digital world hangs in the balance.
Table of Contents
- Cybercriminals are weaponizing the AI
- Consequences of AI-powered cyberattacks
- Consequences of AI-Powered Cyberattacks in Data Breaches
- Consequences of AI-powered Cyberattacks in Financial Losses
- Consequences of AI-powered Cyberattacks in Reputational Damage
- Consequences of AI-powered Cyberattacks in Operational Disruption
- Consequences of AI-powered Cyberattacks in National Security Threats
- Combating the AI-Powered Cyberattacks
- Conclusion
Cybercriminals are weaponizing the AI
AI algorithms can be trained to analyze vast amounts of data, identify patterns, and make predictions with remarkable accuracy. Cybercriminals are exploiting these capabilities to automate and enhance their attacks in several ways:
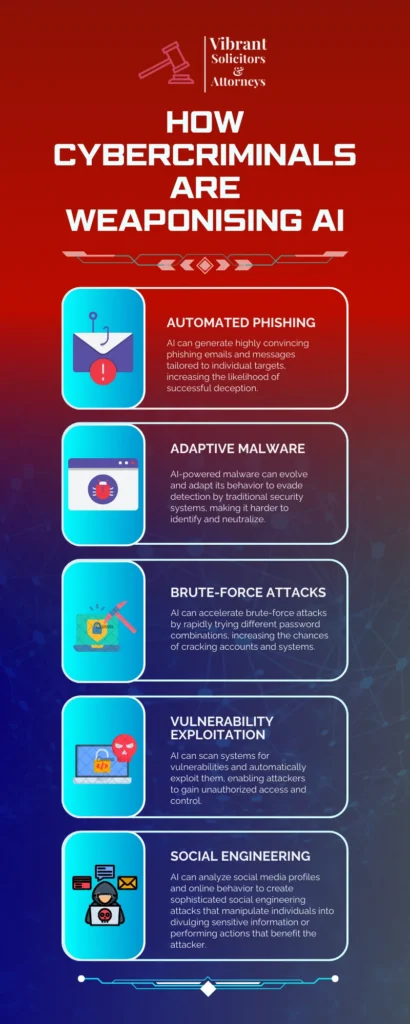
The misuse of AI in Automated Phishing
AI can be misused for automated phishing in several ways, significantly increasing the scale and effectiveness of these attacks:
1. Crafting Convincing Content:
- Personalized Emails: AI can analyze vast datasets of personal information (scraped from social media, data breaches, etc.) to create highly personalized phishing emails. These emails might reference specific details about the target, like recent purchases, job titles, or interests, making them appear more legitimate and increasing the chance of the recipient clicking on malicious links or attachments.
- Generating Human-like Text: AI-powered language models can generate grammatically correct and natural-sounding text that mimics human writing styles. This makes it harder to detect phishing emails based on awkward phrasing or grammatical errors, which are common in traditional phishing attempts.
- Dynamic Content Adaptation: AI can analyze the recipient’s responses and adapt the phishing content in real-time. For example, if the victim expresses skepticism, the AI can generate new text to address their concerns and further build trust.
2. Scaling and Automating Attacks:
- Mass Personalization: AI can personalize phishing emails at scale, allowing attackers to target thousands or even millions of individuals with unique messages tailored to their specific profiles.
- Automated Email Sending: AI can automate the process of sending phishing emails, eliminating the need for manual intervention and allowing attackers to launch large-scale campaigns with minimal effort.
- Bot-powered Interaction: AI-powered chatbots can engage with victims in real-time, answering questions and providing information that reinforces the legitimacy of the phishing attempt.
3. Evading Detection:

- Bypassing Spam Filters: AI can analyze spam filters and adapt the content of phishing emails to evade detection. This might involve using different wording, avoiding trigger words, or manipulating email headers.
- Mimicking Legitimate Websites: AI can be used to create convincing fake websites that closely resemble legitimate ones. These websites might be used to harvest login credentials or other sensitive information.
Ethical Concerns:
The use of AI in automated phishing raises serious ethical concerns. It enables attackers to conduct highly effective and targeted attacks, putting individuals and organizations at greater risk.
It also makes it more difficult for people to distinguish between legitimate and malicious communications, eroding trust in online interactions.

It’s crucial to be aware of these threats and take steps to protect yourself, such as being cautious of unsolicited emails, verifying the sender’s identity, and using strong passwords and multi-factor authentication.
The misuse of AI in Adaptive Malware
AI can be used to create “adaptive malware” that is more sophisticated, evasive, and destructive than traditional malware. Here’s how:
1. Evading Detection:

- Polymorphic Code: AI can be used to generate polymorphic code, which changes its structure and appearance each time it spreads. This makes it difficult for traditional security solutions that rely on signature-based detection to identify and block the malware.
- Behavior Learning: AI algorithms can analyze the behavior of security software and adapt the malware’s actions to avoid detection. For example, the malware might delay its malicious activities or mimic benign processes to blend in with normal system operations.
- Anti-Sandboxing Techniques: AI can enable malware to detect if it’s running in a sandbox environment (a controlled environment used to analyze malware). If detected, the malware can alter its behavior to avoid revealing its true purpose, making analysis more difficult.
2. Maximizing Impact:
- Targeted Attacks: AI can analyze a system’s vulnerabilities and tailor the malware’s attack strategy to exploit specific weaknesses. This allows the malware to inflict maximum damage or gain access to the most valuable data.
- Lateral Movement: Once inside a network, AI-powered malware can analyze network traffic and identify vulnerable systems to spread to. This allows the malware to propagate quickly and compromise multiple devices.
- Data Exfiltration: AI can be used to identify and prioritize valuable data for exfiltration. The malware can then stealthily extract this data without raising suspicion.

3. Self-Learning and Evolution:

Reinforcement Learning: AI algorithms can use reinforcement learning to continuously improve the malware’s effectiveness. By analyzing the outcomes of its actions, the malware can learn which techniques are most successful and adapt its behavior accordingly.
Automated Updates: AI can enable malware to automatically update itself with new features, exploits, and evasion techniques. This makes it a constantly evolving threat that is difficult to defend against.
Challenges and Concerns:
The use of AI in adaptive malware poses significant challenges for cybersecurity professionals. Traditional security solutions may be ineffective against these advanced threats, requiring new approaches to detection and prevention.
Additionally, the ability of AI-powered malware to learn and evolve raises concerns about the potential for increasingly sophisticated and damaging attacks in the future.

It’s crucial for individuals and organizations to stay informed about these threats and invest in advanced security solutions that can detect and respond to AI-powered malware.
The misuse of AI in Brute-Force Attacks
While brute-force attacks are nothing new, AI is giving this age-old technique a dangerous upgrade. Here’s how AI is being misused to supercharge brute-force attacks:
1. Optimizing Guessing Strategies:

- Pattern Recognition: AI algorithms can analyze vast datasets of leaked passwords and identify common patterns, such as the use of dictionary words, common substitutions (e.g., “@” for “a”), and sequential keyboard patterns. This allows the AI to prioritize guesses that are more likely to be successful, significantly reducing the time it takes to crack a password.
- Learning from Successes and Failures: AI can use machine learning to learn from previous attempts, identifying which guessing strategies are most effective and refining its approach over time. This allows the AI to adapt to different password complexities and security measures.
- Predicting Password Composition: AI can analyze user data, such as online behavior, interests, and demographics, to predict the likely composition of their passwords. This allows for more targeted guessing, further increasing the chances of success.
2. Increasing Speed and Scale:
- Parallel Processing: AI can leverage the power of parallel processing to try multiple password combinations simultaneously, dramatically increasing the speed of the attack.
- Distributed Computing: AI can distribute the brute-force attack across a network of computers or devices, further amplifying its power and making it harder to defend against.
- Cloud Computing: Attackers can utilize cloud computing resources to launch massive-scale brute-force attacks, leveraging the vast processing power and scalability of cloud platforms.

3. Bypassing Security Measures:

- Account Lockout Evasion: AI can be used to identify and circumvent account lockout mechanisms, which are designed to prevent brute-force attacks by locking an account after a certain number of failed login attempts. For example, the AI might slow down the attack or use multiple IP addresses to avoid triggering the lockout.
- CAPTCHA Circumvention: AI-powered image recognition can be used to solve CAPTCHAs, which are often used to prevent automated attacks. This allows the AI to continue the brute-force attack without human intervention.
4. Targeting Weak Points:
- Exploiting Human Behavior: AI can analyze user behavior to identify weak points in password security practices, such as the reuse of passwords across multiple accounts or the use of easily guessable passwords. This allows the AI to focus its efforts on the most vulnerable targets.
- Identifying Vulnerable Systems: AI can scan networks and systems for weak passwords or outdated security protocols, allowing attackers to target the most vulnerable entry points.

Consequences and Mitigation:
The use of AI in brute-force attacks poses a significant threat to online security. It enables attackers to crack passwords more quickly and efficiently, increasing the risk of unauthorized access to accounts and systems. This can lead to data breaches, financial losses, and reputational damage.

To mitigate these risks, it is crucial to use strong, unique passwords for each account, enable multi-factor authentication whenever possible, and keep software and systems updated with the latest security patches.
Additionally, organizations should invest in robust security solutions that can detect and prevent brute-force attacks, such as intrusion detection systems and AI-powered threat intelligence platforms.
The misuse of AI in Vulnerability Exploitation
The misuse of AI in vulnerability exploitation is a growing concern as it allows attackers to automate the process of identifying and exploiting weaknesses in systems and applications, leading to more efficient and widespread cyberattacks.
Here’s a breakdown of how AI is being misused in this area:
1. Automated Vulnerability Discovery:
Scanning and Analysis: AI algorithms can be trained to analyze vast amounts of code, network traffic, and system configurations to identify potential vulnerabilities. This automation allows attackers to scan for weaknesses much faster and more comprehensively than traditional methods.
Pattern Recognition: AI can identify patterns and anomalies that may indicate vulnerabilities, even in complex systems. This allows it to pinpoint potential weaknesses that might be missed by human analysts.
Zero-Day Vulnerability Discovery: AI can potentially discover previously unknown vulnerabilities (zero-day exploits) by analyzing code and identifying weaknesses that haven’t been publicly disclosed or patched.

2. Exploit Development:

- Automated Exploit Generation: AI can be used to automatically generate exploits for known vulnerabilities. This significantly reduces the time and effort required to weaponize a vulnerability, making attacks more rapid and widespread.
- Polymorphic Exploits: AI can create polymorphic exploits that change their structure and behavior to evade detection by security systems. This makes it more difficult to defend against attacks as traditional signature-based detection methods become less effective.
- Context-Aware Exploits: AI can analyze the target system and tailor the exploit to specific configurations and vulnerabilities, increasing the chances of successful exploitation.
3. Attack Execution and Management:

- Automated Attack Launching: AI can automate the process of launching attacks, allowing attackers to exploit vulnerabilities on a massive scale with minimal human intervention.
- Lateral Movement: Once a vulnerability is exploited, AI can be used to navigate through the compromised network, identify other vulnerable systems, and spread the attack laterally.
- Evasion Techniques: AI can enable malware to evade detection by security systems by adapting its behavior, hiding its presence, and disabling security tools.
Consequences and Mitigation:
The misuse of AI in vulnerability exploitation poses a significant threat to cybersecurity. It enables attackers to launch more sophisticated, targeted, and widespread attacks, potentially causing significant damage to individuals, organizations, and critical infrastructure.
To mitigate these risks, it’s crucial to:
- Prioritize Vulnerability Management: Implement robust vulnerability management programs that include regular scanning, patching, and mitigation of identified weaknesses.
- Invest in AI-Powered Security Solutions: Utilize AI-powered security tools that can detect and respond to sophisticated attacks, including those that exploit zero-day vulnerabilities.
- Employ Threat Intelligence: Stay informed about the latest threats and vulnerabilities by leveraging threat intelligence platforms and collaborating with security researchers and industry partners.
- Enhance Security Awareness: Educate users and employees about cybersecurity best practices and the importance of reporting suspicious activity.

By combining proactive measures, advanced security technologies, and ongoing vigilance, we can better defend against the growing threat of AI-powered vulnerability exploitation.
The misuse of AI in Social Engineering
AI is being weaponized to make social engineering attacks more sophisticated, personalized, and effective. Here’s how:
1. Information Gathering and Profiling:

- Social Media Analysis: AI algorithms can analyze social media profiles, posts, and interactions to gather information about an individual’s interests, relationships, and online behavior. This information can be used to craft highly targeted social engineering attacks that exploit the victim’s trust and vulnerabilities.
- Data Mining: AI can sift through vast amounts of data from various sources, including data breaches, public records, and online forums, to create detailed profiles of potential victims. This allows attackers to identify individuals who are more susceptible to social engineering tactics.
- Behavioral Analysis: AI can analyze online behavior, such as browsing history, search queries, and email interactions, to identify patterns and predict future actions. This information can be used to anticipate a victim’s responses and tailor the social engineering attack accordingly.
2. Creating Convincing Personas and Content:
- Deepfakes: AI-powered deepfake technology can create highly realistic fake videos and audio recordings of individuals, which can be used to impersonate trusted figures or manipulate victims into believing fabricated scenarios.
- Natural Language Generation: AI can generate human-like text that is grammatically correct and emotionally persuasive. This can be used to craft compelling phishing emails, social media messages, or chat conversations that lure victims into divulging sensitive information or performing actions that benefit the attacker.
- Personalized Content: AI can personalize social engineering attacks by tailoring the content to the victim’s specific interests, concerns, and vulnerabilities. This makes the attack more convincing and increases the likelihood of success.

3. Automating and Scaling Attacks:
- Chatbots: AI-powered chatbots can engage with victims in real-time, answering questions, providing information, and building rapport. This can be used to automate social engineering attacks and interact with multiple victims simultaneously.
- Automated Phishing Campaigns: AI can automate the process of sending phishing emails and social media messages, allowing attackers to launch large-scale campaigns with minimal effort.
- Adaptive Attacks: AI can analyze a victim’s responses and adapt the social engineering attack in real-time. This allows the attacker to adjust their tactics and maintain the deception, even if the victim expresses skepticism.
Consequences and Mitigation:
The misuse of AI in social engineering poses a significant threat to individuals and organizations. It enables attackers to launch highly targeted and convincing attacks that can bypass traditional security measures and exploit human vulnerabilities. This can lead to data breaches, financial losses, and reputational damage.
To mitigate these risks, it’s crucial to:
- Educate and Train: Educate users and employees about social engineering tactics and how to identify potential threats.
- Promote Skepticism: Encourage a culture of skepticism and critical thinking when interacting with online content and communications.
- Verify Information: Always verify the identity of individuals and the legitimacy of requests before sharing sensitive information or performing actions.
- Implement Security Measures: Implement strong authentication mechanisms, such as multi-factor authentication, to protect accounts and systems from unauthorized access.
- Utilize AI-Powered Defenses: Invest in AI-powered security solutions that can detect and prevent social engineering attacks by analyzing communication patterns, identifying suspicious behavior, and flagging potential threats.

By combining education, awareness, and advanced security technologies, we can better protect ourselves from the evolving threat of AI-powered social engineering attacks.
Consequences of AI-powered cyberattacks
The implications of AI-powered cyberattacks are significant. They can lead to:
- Data Breaches: Compromised sensitive data, including personal information, financial records, and intellectual property.
- Financial Losses: Stolen funds, disrupted operations, and costly recovery efforts.
- Reputational Damage: Loss of trust, customer churn, and negative media attention.
- Operational Disruption: Disrupted critical infrastructure, halted services, and impaired business continuity.
- National Security Threats: Compromised national security systems and sensitive information.

Consequences of AI-Powered Cyberattacks in Data Breaches
AI-powered cyberattacks are revolutionizing the way data breaches occur, making them more sophisticated, targeted, and damaging.
Here’s a breakdown of the consequences:
1. Increased Scale and Scope of Breaches:
- Automation: AI enables attackers to automate various stages of the attack process, from identifying vulnerabilities to exfiltrating data. This allows them to compromise a larger number of systems and steal vast amounts of data quickly and efficiently.
- Scalability: AI-powered attacks can be easily scaled up to target multiple organizations or individuals simultaneously, leading to widespread data breaches with far-reaching consequences.
2. More Sophisticated Targeting:
- Personalized Attacks: AI can analyze vast amounts of data to identify and exploit specific vulnerabilities in individuals and organizations. This allows attackers to tailor their attacks, increasing the chances of success and maximizing the impact of the breach.
- Predictive Targeting: AI can analyze patterns and predict future behavior, enabling attackers to anticipate security measures and circumvent them. This makes it harder for organizations to defend against data breaches.
3. Enhanced Evasion Techniques:
- Adaptive Malware: AI-powered malware can evolve and adapt its behavior to evade detection by traditional security systems. This makes it more difficult to identify and contain data breaches, allowing attackers to remain undetected for longer periods.
- Anti-forensic Techniques: AI can be used to cover the tracks of an attack, making it harder for investigators to trace the source of the breach and identify the perpetrators.
4. Exfiltration of High-Value Data:
- Data Prioritization: AI can analyze data and identify high-value information, such as financial records, intellectual property, and sensitive personal data. This allows attackers to prioritize the exfiltration of the most valuable data, maximizing the impact of the breach.
- Stealthy Exfiltration: AI can enable attackers to exfiltrate data stealthily, avoiding detection by security systems and minimizing the risk of interruption.
5. Long-Term Impact:
- Reputational Damage: Data breaches can severely damage an organization’s reputation, leading to loss of trust, customer churn, and negative media attention.
- Financial Losses: Data breaches can result in significant financial losses due to stolen funds, legal fees, regulatory fines, and the cost of recovery efforts.
- Operational Disruption: Data breaches can disrupt critical operations, leading to downtime, service interruptions, and loss of productivity.
- Legal and Regulatory Consequences: Organizations may face legal and regulatory consequences for failing to protect sensitive data, including fines, penalties, and lawsuits.
Mitigating the Impact of AI-Powered Cyberattacks in Data Breaches:
To mitigate the impact of AI-powered data breaches, organizations need to adopt a proactive and multi-layered approach to cybersecurity:
- Invest in AI-Powered Security Solutions: Implement AI-powered security tools that can detect and respond to sophisticated attacks, including those that utilize AI.
- Strengthen Data Security: Implement robust data security measures, including encryption, access controls, and data loss prevention (DLP) solutions.
- Enhance Incident Response: Develop and regularly test incident response plans to ensure a swift and effective response to data breaches.
- Employee Education and Training: Educate employees about cybersecurity best practices and the importance of data security.
- Collaboration and Information Sharing: Share threat intelligence and collaborate with industry partners and government agencies to enhance collective defense.
By staying vigilant, adopting proactive measures, and fostering collaboration, organizations can better protect themselves from the growing threat of AI-powered data breaches and minimize the impact of these attacks.
Consequences of AI-powered Cyberattacks in Financial Losses
AI-powered cyberattacks are a growing threat to businesses and individuals, leading to significant financial losses across various sectors.
Here’s a breakdown of the financial consequences:
1. Direct Financial Theft:
- Account Takeovers: AI can facilitate account takeovers through sophisticated phishing attacks, credential stuffing, and brute-force attacks, allowing attackers to gain access to bank accounts, investment portfolios, and online payment systems. This can lead to direct theft of funds, unauthorized transactions, and fraudulent activities.
- Ransomware Attacks: AI-powered ransomware can identify and encrypt critical data, disrupting operations and extorting ransoms from victims. The cost of recovering from a ransomware attack can be substantial, including ransom payments, downtime, data recovery expenses, and legal fees.
- Cryptocurrency Theft: AI can be used to identify and exploit vulnerabilities in cryptocurrency exchanges, wallets, and trading platforms, leading to theft of digital assets. The volatile nature of cryptocurrencies can amplify financial losses due to price fluctuations.
2. Business Disruption and Lost Revenue:
- Denial-of-Service Attacks: AI-powered DDoS attacks can overwhelm online services, disrupting operations and preventing customers from accessing websites and applications. This can lead to lost revenue, damage to reputation, and customer churn.
- Supply Chain Attacks: AI can be used to identify and exploit vulnerabilities in supply chains, disrupting production, distribution, and logistics. This can lead to delays, lost productivity, and financial losses for businesses across the supply chain.
- Data Breaches: AI-powered data breaches can expose sensitive financial data, leading to regulatory fines, legal fees, and the cost of credit monitoring and identity theft protection for affected individuals.
3. Increased Operational Costs:
- Security Investments: Organizations need to invest in advanced security solutions, such as AI-powered threat detection and response systems, to defend against AI-powered cyberattacks. These investments can be substantial, especially for small and medium-sized businesses.
- Incident Response and Recovery: The cost of responding to and recovering from AI-powered cyberattacks can be significant, including forensic investigations, data recovery, system restoration, and legal and public relations expenses.
- Insurance Premiums: Cyber insurance premiums are likely to increase as the frequency and severity of AI-powered cyberattacks rise, adding to the financial burden for businesses.
4. Long-Term Financial Impact:
- Reputational Damage: Financial losses from AI-powered cyberattacks can extend beyond immediate costs, as reputational damage can lead to loss of trust, customer churn, and decreased investor confidence.
- Competitive Disadvantage: Businesses that suffer significant financial losses from cyberattacks may struggle to compete with rivals who have invested more in cybersecurity and resilience.
- Economic Impact: The cumulative financial losses from AI-powered cyberattacks can have a significant impact on the global economy, hindering innovation, investment, and growth.
Mitigating Financial Losses from AI-Powered Cyberattacks
To mitigate the financial losses associated with AI-powered cyberattacks, organizations need to adopt a proactive and comprehensive approach to cybersecurity:
- Invest in AI-Powered Security: Implement AI-powered security solutions to detect and respond to sophisticated threats in real-time.
- Strengthen Cybersecurity Posture: Implement robust cybersecurity measures, including multi-factor authentication, access controls, and data encryption.
- Develop Incident Response Plans: Create and regularly test incident response plans to ensure a swift and effective response to cyberattacks.
- Employee Education and Awareness: Train employees on cybersecurity best practices and the importance of vigilance.
- Collaboration and Information Sharing: Share threat intelligence and collaborate with industry partners and government agencies to enhance collective defense.
By proactively addressing the evolving threat of AI-powered cyberattacks, organizations can minimize financial losses, protect their reputation, and ensure business continuity.
Consequences of AI-powered Cyberattacks in Reputational Damage
AI-powered cyberattacks can inflict severe reputational damage on individuals and organizations, eroding trust, alienating customers, and impacting long-term success.
Here’s a breakdown of the consequences:
1. Loss of Trust:
- Data Breaches: When sensitive information is compromised in an AI-powered attack, customers and partners may lose trust in the organization’s ability to protect their data. This can lead to decreased customer loyalty, reluctance to share information, and potential legal action.
- Manipulation and Deception: AI can be used to create convincing deepfakes and spread misinformation, damaging the reputation of individuals and organizations by associating them with false or misleading content. This can erode public trust and create doubt about their integrity.
2. Customer Churn and Loss of Business:
- Negative Publicity: AI-powered attacks often attract significant media attention, highlighting security vulnerabilities and amplifying the negative impact on reputation. This can lead to customer churn, boycotts, and loss of business opportunities.
- Competitive Disadvantage: Reputational damage can give competitors a significant advantage, as customers may migrate to businesses perceived as more secure and trustworthy. This can impact market share, revenue, and long-term growth prospects.
3. Impact on Brand Image and Value:
- Brand Erosion: A damaged reputation can erode brand image and value, diminishing the perceived quality, reliability, and trustworthiness of products and services. This can negatively impact brand equity and future marketing efforts.
- Investor Confidence: Reputational damage can also affect investor confidence, leading to decreased investment, lower stock prices, and difficulty attracting funding for future projects.
4. Social Media Amplification:
- Rapid Dissemination: Social media platforms can rapidly amplify the negative impact of AI-powered attacks, spreading news of data breaches, misinformation, and customer complaints to a wide audience. This can quickly escalate reputational damage and create a crisis situation.
- Online Backlash: Social media can also fuel online backlash, with customers expressing their dissatisfaction, sharing negative experiences, and organizing campaigns against the affected organization. This can further damage reputation and prolong the recovery process.
5. Long-Term Consequences:
- Difficulty Rebuilding Trust: Rebuilding trust after a reputational damaging cyberattack can be a long and challenging process, requiring significant investment in security measures, communication, and customer outreach.
- Lost Opportunities: Reputational damage can hinder future opportunities, such as partnerships, collaborations, and expansion into new markets.
- Legal and Regulatory Challenges: Organizations may face legal challenges and regulatory scrutiny following an AI-powered attack, leading to fines, penalties, and increased oversight.
Mitigating Reputational Damage from AI-Powered Cyberattacks
To mitigate reputational damage from AI-powered cyberattacks, organizations should:
- Prioritize Cybersecurity: Invest in robust cybersecurity measures, including AI-powered threat detection and response systems, to prevent attacks and protect sensitive data.
- Develop a Crisis Communication Plan: Prepare a comprehensive crisis communication plan to respond quickly and effectively to cyberattacks, addressing public concerns and managing media narratives.
- Be Transparent and Accountable: Communicate openly and honestly with customers and stakeholders about the attack, the impact, and the steps being taken to address the situation.
- Invest in Reputation Management: Engage in proactive reputation management efforts to monitor online sentiment, address negative feedback, and rebuild trust with customers and partners.
- Foster a Culture of Security: Promote a culture of security awareness among employees, encouraging vigilance, reporting suspicious activity, and adhering to cybersecurity best practices.
By taking proactive steps to prevent attacks, respond effectively to incidents, and manage reputation proactively, organizations can minimize the reputational damage caused by AI-powered cyberattacks and protect their long-term success.
Consequences of AI-powered Cyberattacks in Operational Disruption
AI-powered cyberattacks are increasingly capable of causing significant operational disruptions, impacting businesses, critical infrastructure, and essential services.
Here’s a detailed look at the consequences:
1. Disruption of Critical Infrastructure:
- Targeting Essential Services: AI can be used to identify and exploit vulnerabilities in critical infrastructure systems, such as power grids, transportation networks, healthcare facilities, and financial institutions.1 Attacks on these systems can cause widespread disruptions, impacting essential services and public safety.
- Manipulating Industrial Control Systems: AI-powered attacks can target industrial control systems (ICS) used in manufacturing, energy production, and other critical sectors. By manipulating these systems, attackers can disrupt production processes, damage equipment, and even cause physical harm.
2. Business Downtime and Service Interruptions:
- Denial-of-Service Attacks: AI-powered DDoS attacks can overwhelm online services, causing websites, applications, and critical business systems to become unavailable. This can disrupt operations, prevent customers from accessing services, and lead to significant financial losses.
- Ransomware Attacks: AI-powered ransomware can encrypt critical data and systems, effectively shutting down operations until a ransom is paid. The downtime caused by ransomware attacks can be substantial, impacting productivity, revenue, and customer satisfaction.
3. Disruption of Supply Chains:
- Targeting Supply Chain Vulnerabilities: AI can be used to identify and exploit vulnerabilities in supply chains, disrupting the flow of goods, materials, and information. This can lead to delays, shortages, and increased costs for businesses across the supply chain.
- Compromising Logistics and Transportation: AI-powered attacks can target logistics and transportation systems, disrupting the movement of goods and impacting delivery schedules. This can cause significant disruptions for businesses that rely on timely deliveries and efficient supply chain operations.
4. Impact on Internal Operations:
- Disrupting Communication and Collaboration: AI-powered attacks can disrupt internal communication and collaboration tools, hindering productivity and decision-making. This can impact employee morale, project timelines, and overall business efficiency.
- Compromising Internal Systems: Attacks on internal systems, such as email servers, file-sharing platforms, and databases, can disrupt daily operations, limit access to critical information, and hinder employee productivity.
5. Impact on Healthcare:
- Disrupting Patient Care: AI-powered attacks on healthcare systems can disrupt patient care by compromising electronic health records (EHRs), medical devices, and communication systems. This can delay treatments, impact diagnoses, and even put patients’ lives at risk.
- Compromising Medical Research: Attacks on research institutions and pharmaceutical companies can disrupt medical research, delaying the development of new treatments and impacting public health.
Mitigating Operational Disruption from AI-Powered Cyberattacks
To mitigate the risk of operational disruption from AI-powered cyberattacks, organizations should:
- Invest in Robust Cybersecurity: Implement AI-powered security solutions to detect and respond to sophisticated threats in real-time.
- Secure Critical Infrastructure: Prioritize the security of critical infrastructure systems, implementing strong access controls, network segmentation, and intrusion detection systems.
- Develop Business Continuity Plans: Create and regularly test business continuity plans to ensure operational resilience in the event of a cyberattack.
- Secure Supply Chains: Collaborate with suppliers and partners to secure supply chains, implementing security standards and sharing threat intelligence.
- Employee Training and Awareness: Educate employees about cybersecurity best practices and the importance of reporting suspicious activity.
By proactively addressing the evolving threat of AI-powered cyberattacks, organizations can minimize operational disruptions, protect critical infrastructure, and ensure business continuity.
Consequences of AI-powered Cyberattacks in National Security Threats
AI-powered cyberattacks pose a significant and evolving threat to national security, with potential consequences ranging from espionage and sabotage to disruption of critical infrastructure and manipulation of public opinion.
Here’s a detailed look at the key concerns:
1. Espionage and Information Warfare:
- Advanced Persistent Threats (APTs): AI can enable highly sophisticated APTs that can infiltrate government networks, steal sensitive information, and remain undetected for extended periods. This can compromise national secrets, military plans, and critical intelligence, potentially jeopardizing national security.
- Disinformation Campaigns: AI-powered tools can be used to generate and spread disinformation at scale, manipulating public opinion, influencing elections, and undermining trust in government institutions. This can destabilize nations, incite social unrest, and create vulnerabilities that adversaries can exploit.
2. Sabotage and Disruption of Critical Infrastructure:
- Targeting Critical Systems: AI can be used to identify and exploit vulnerabilities in critical infrastructure systems, such as power grids, transportation networks, communication systems, and financial institutions. Successful attacks on these systems can cause widespread disruption, economic damage, and even loss of life, posing a direct threat to national security.
- Weaponizing Autonomous Systems: AI is increasingly being integrated into autonomous systems, such as drones and military vehicles. If compromised, these systems could be weaponized against a nation’s own forces or civilian population, causing significant damage and casualties.
3. Escalation of Cyber Warfare:
- Automated Attacks: AI can automate various stages of cyberattacks, making them faster, more efficient, and harder to defend against. This could lead to an escalation of cyber warfare, with nations launching rapid and devastating attacks against each other’s critical infrastructure and digital assets.
- AI-Powered Arms Race: The development and deployment of AI-powered cyber weapons could trigger an AI arms race, with nations competing to develop more sophisticated and destructive tools. This could increase the risk of unintended escalation and potentially lead to catastrophic consequences.
4. Erosion of Trust and Social Cohesion:
- Deepfakes and Synthetic Media: AI-powered deepfakes can create highly realistic fake videos and audio recordings, potentially undermining trust in government officials, spreading false narratives, and inciting social unrest. This can erode social cohesion and create vulnerabilities that adversaries can exploit.
- Cyber-Enabled Influence Operations: AI can be used to conduct sophisticated influence operations, targeting specific demographics with personalized disinformation and propaganda. This can manipulate public opinion, sow discord, and interfere with democratic processes, threatening national security and stability.
5. Economic and Geopolitical Instability:
- Disrupting Global Markets: AI-powered attacks on financial institutions and critical infrastructure can disrupt global markets, causing economic instability and undermining confidence in national economies. This can have far-reaching consequences for national security and international relations.
- Shifting Global Power Dynamics: The development and deployment of AI-powered cyber capabilities could shift global power dynamics, giving nations with advanced AI capabilities a significant advantage in cyberspace. This could destabilize existing alliances and create new geopolitical tensions.
Mitigating National Security Threats from AI-Powered Cyberattacks
To mitigate the national security threats posed by AI-powered cyberattacks, nations need to:
- Invest in AI Cybersecurity: Develop and deploy AI-powered cybersecurity tools to detect and defend against sophisticated attacks.
- Strengthen Critical Infrastructure Protection: Prioritize the security of critical infrastructure systems, implementing robust security measures and resilience strategies.
- International Cooperation: Foster international cooperation on cybersecurity, sharing threat intelligence and developing norms of responsible behavior in cyberspace.
- AI Ethics and Regulation: Develop ethical guidelines and regulations for the development and use of AI in cyber operations, ensuring responsible innovation and preventing misuse.
- Public Awareness and Education: Educate the public about the risks of AI-powered cyberattacks and the importance of cybersecurity awareness.
By taking proactive steps to address the evolving threat of AI-powered cyberattacks, nations can protect their national security, maintain stability, and promote a secure and resilient cyberspace.
Combating the AI-Powered Cyberattacks
To combat the growing threat of AI-powered cyberattacks, individuals and organizations need to adopt a proactive and multi-layered approach to cybersecurity. This includes:

- Staying Informed: Keeping abreast of the latest AI-powered attack techniques and trends.
- Investing in Advanced Security Solutions: Implementing AI-powered security tools that can detect and respond to sophisticated threats.
- Strengthening Authentication: Employing multi-factor authentication and strong passwords to protect accounts and systems.
- Educating Users: Training employees and individuals on cybersecurity best practices and how to identify potential threats.
- Collaborating and Sharing Information: Sharing threat intelligence and collaborating with industry partners and government agencies to enhance collective defense.
The rise of AI-powered cyberattacks presents a significant challenge, but by staying vigilant, adopting proactive measures, and fostering collaboration, we can mitigate the risks and protect ourselves from this evolving threat landscape.
Conclusion
The rise of AI-powered cyberattacks presents a formidable challenge to individuals, organizations, and nations alike. As AI technology advances, cybercriminals are leveraging its capabilities to launch increasingly sophisticated, targeted, and damaging attacks.
From automated phishing and adaptive malware to brute-force attacks and vulnerability exploitation, AI is transforming the cyber threat landscape, amplifying the risks and consequences of cybercrime.
The consequences of AI-powered cyberattacks are far-reaching and multifaceted. Data breaches are becoming more prevalent and severe, leading to the exposure of sensitive information, financial losses, and reputational damage.


Operational disruptions are impacting critical infrastructure, businesses, and essential services, causing downtime, service interruptions, and economic losses. National security is threatened by espionage, sabotage, and the potential for AI-powered cyber warfare.
However, the rise of AI-powered cyberattacks is not an insurmountable challenge. By understanding the evolving threat landscape and adopting proactive measures, we can mitigate the risks and protect ourselves from these sophisticated attacks.
This requires a multi-faceted approach that includes:
- Investing in AI-powered security solutions: Implementing advanced security tools that can detect and respond to AI-powered attacks in real-time.
- Strengthening cybersecurity posture: Implementing robust security measures, including multi-factor authentication, access controls, and data encryption.
- Developing incident response plans: Creating and regularly testing incident response plans to ensure a swift and effective response to cyberattacks.
- Educating and raising awareness: Educating employees and the public about cybersecurity best practices, promoting vigilance, and encouraging the reporting of suspicious activity.
- Fostering collaboration and information sharing: Sharing threat intelligence and collaborating with industry partners, government agencies, and international organizations to enhance collective defense.
- Promoting ethical AI development and regulation: Encouraging responsible AI development and implementing regulations to prevent the misuse of AI in cyberattacks.
The future of cybersecurity will be shaped by the ongoing competition between attackers and defenders leveraging AI. By embracing innovation, investing in advanced security technologies, and fostering a culture of cybersecurity awareness, we can navigate this evolving threat landscape and build a more secure and resilient digital future.
The key lies in harnessing the power of AI for good, while proactively addressing the challenges posed by its malicious use. By working together, we can mitigate the risks of AI-powered cyberattacks and ensure a safer digital world for all.
